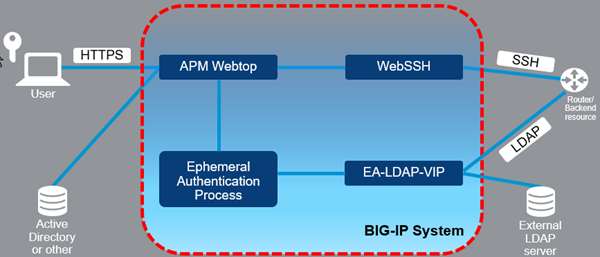
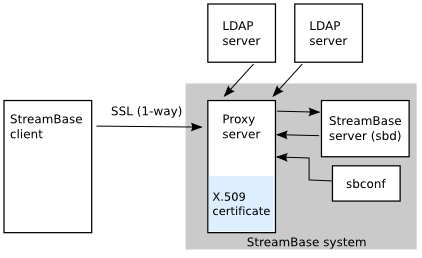
Configuring Proxies for Hybrid Domains within ZENworks Mobile Workspace - ZENworks Tips & Information - ZENworks

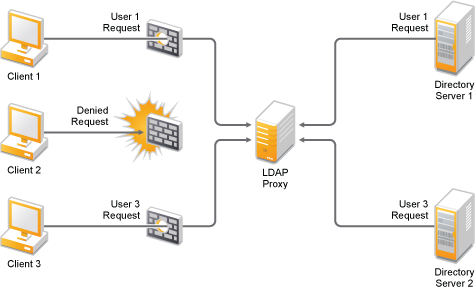
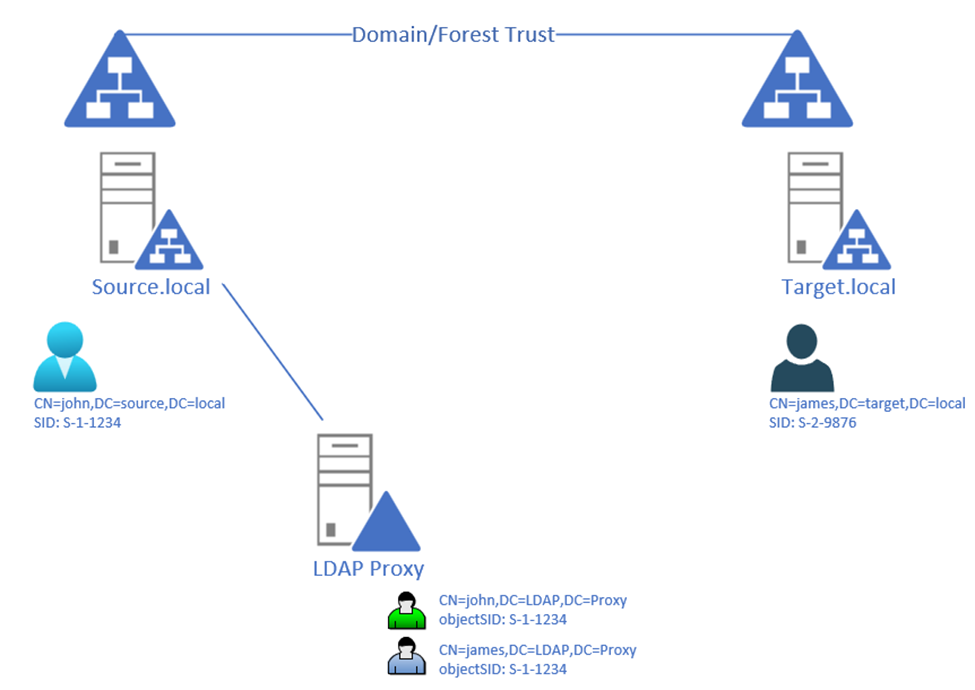
Modernizing your B2C Portal Security - LDAP Proxy for Cloud Identity - IBM Security Identity and Access
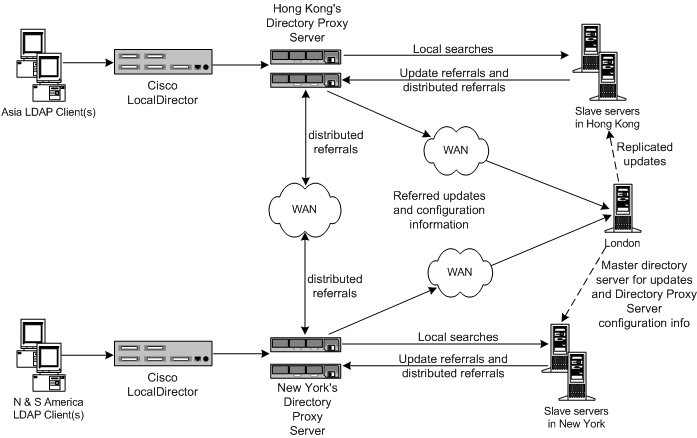
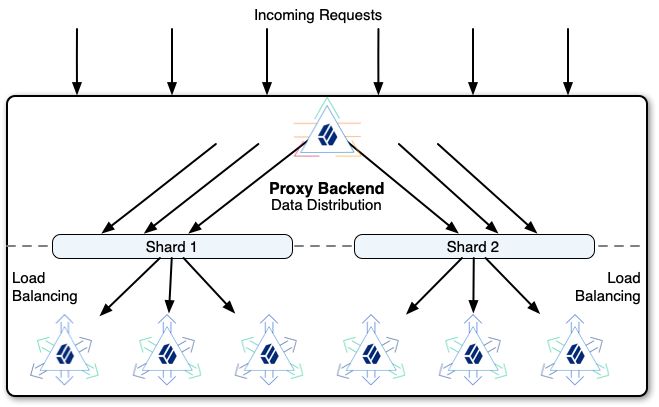
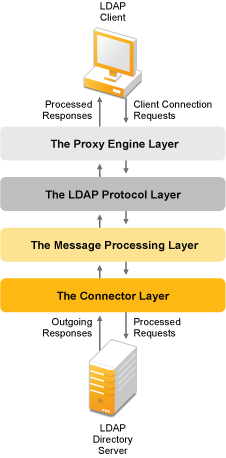
Sun ONE Directory Proxy Server Admistrator's Guide: Chapter 2 Sun ONE Directory Proxy Server Deployment Scenarios
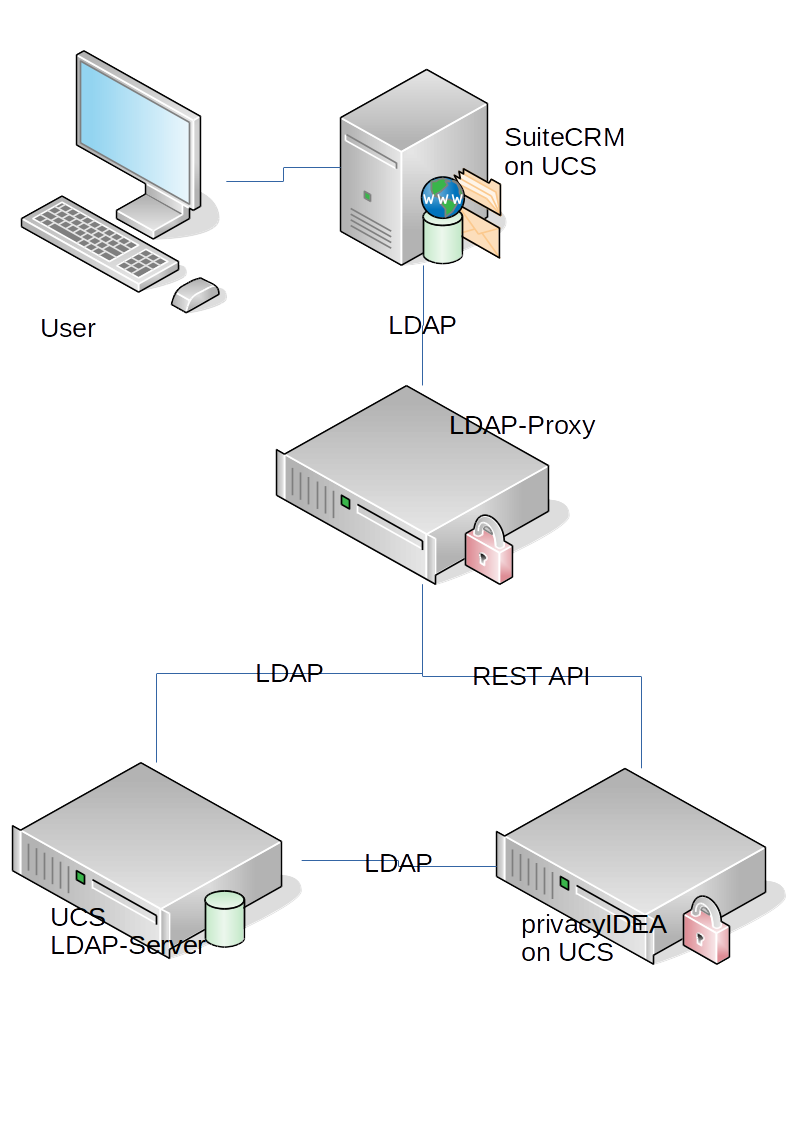
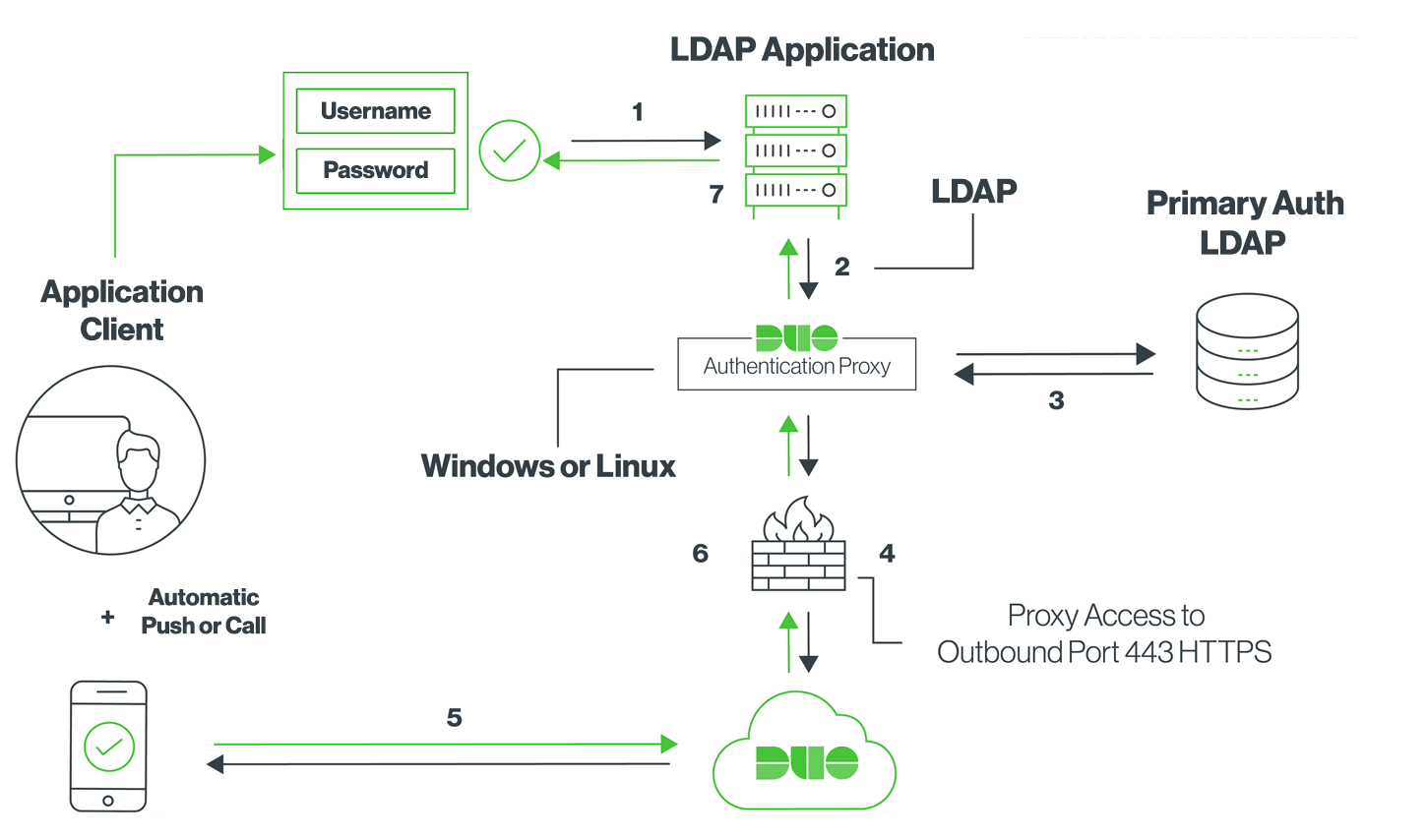
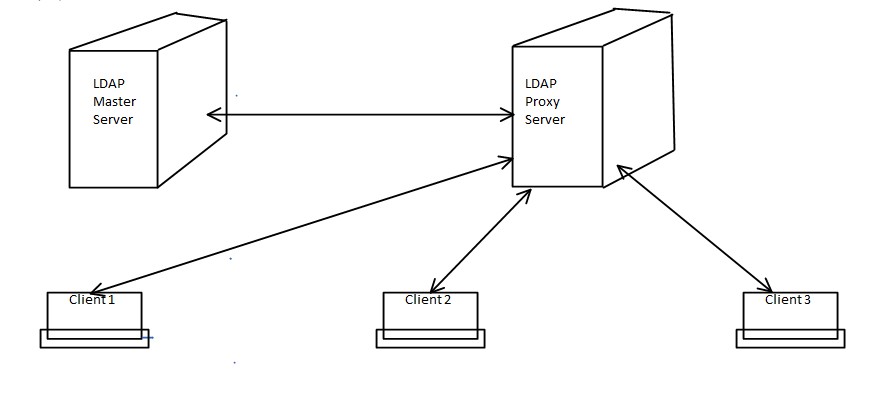
Two factor authentication everywhere with privacyIDEA LDAP-Proxy - NetKnights - IT-Sicherheit - Zwei-Faktor-Authentisierung - Verschlüsselung

GitHub - pinepain/ldap-auth-proxy: A simple drop-in HTTP proxy for transparent LDAP authentication which is also a HTTP auth backend.